AI - Powered Penetration Testing
Smarter Security Starts with Smarter Testing
Why chase threats the old way? Our AI does the heavy lifting — finding flaws faster and smarter — so you can focus on fixing what actually matters.

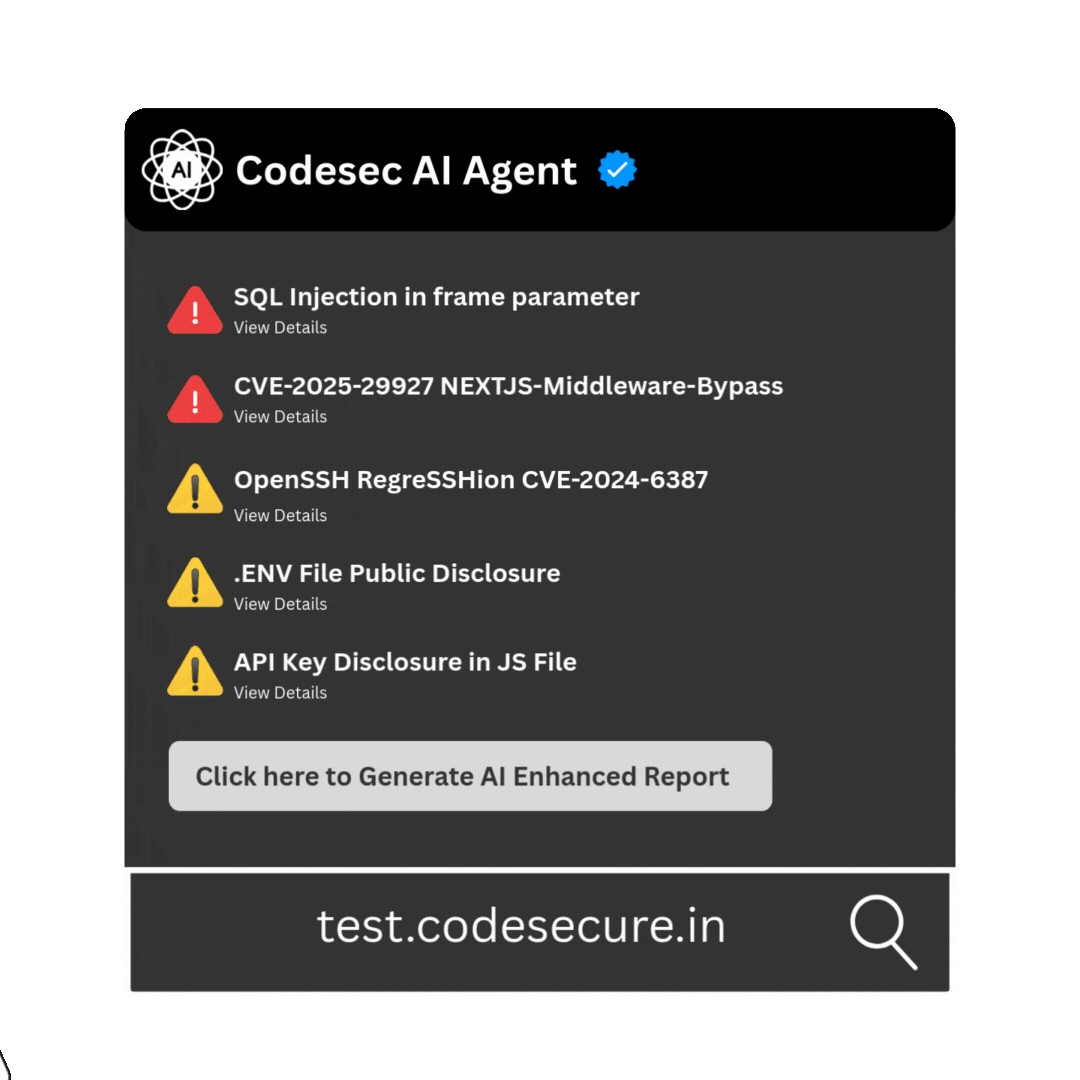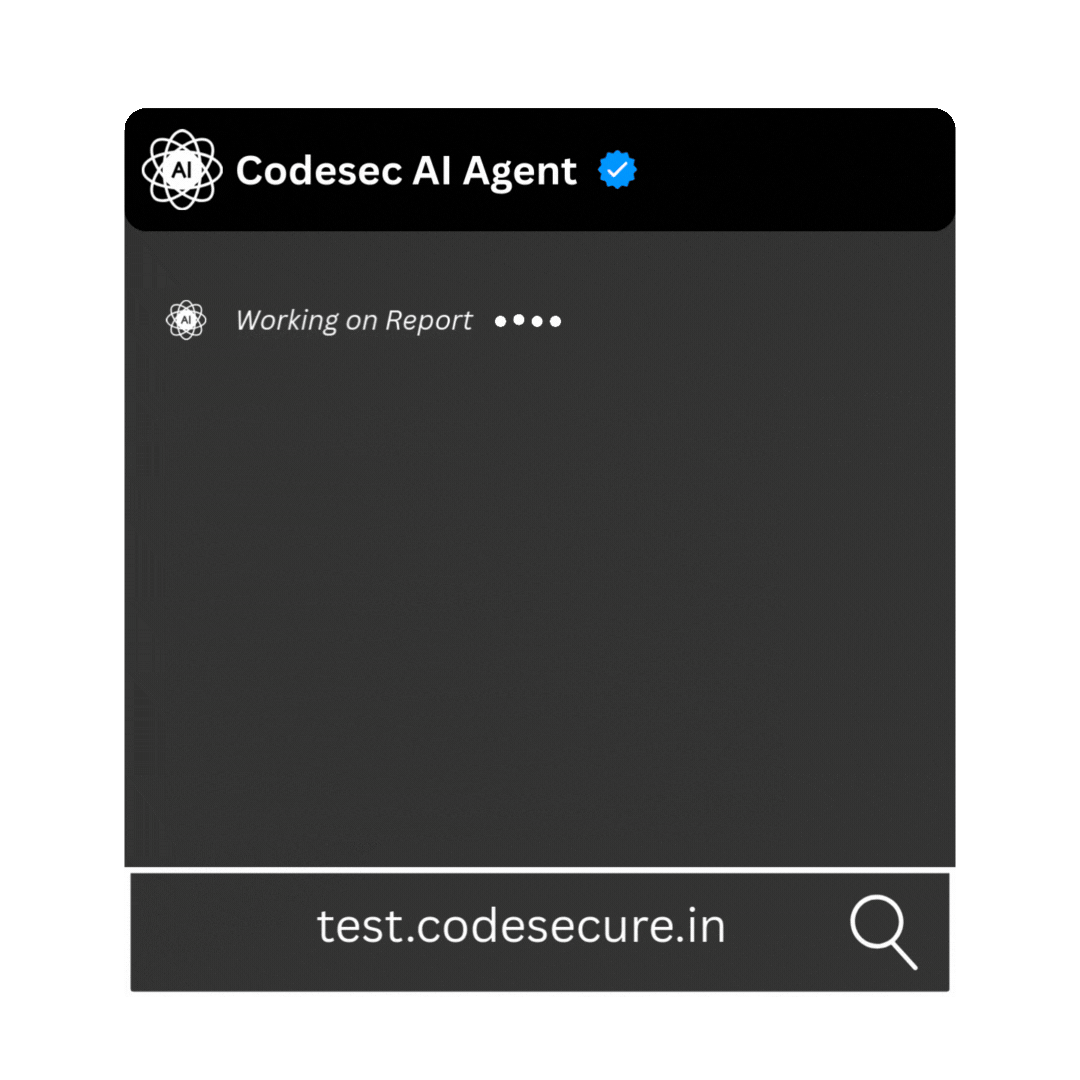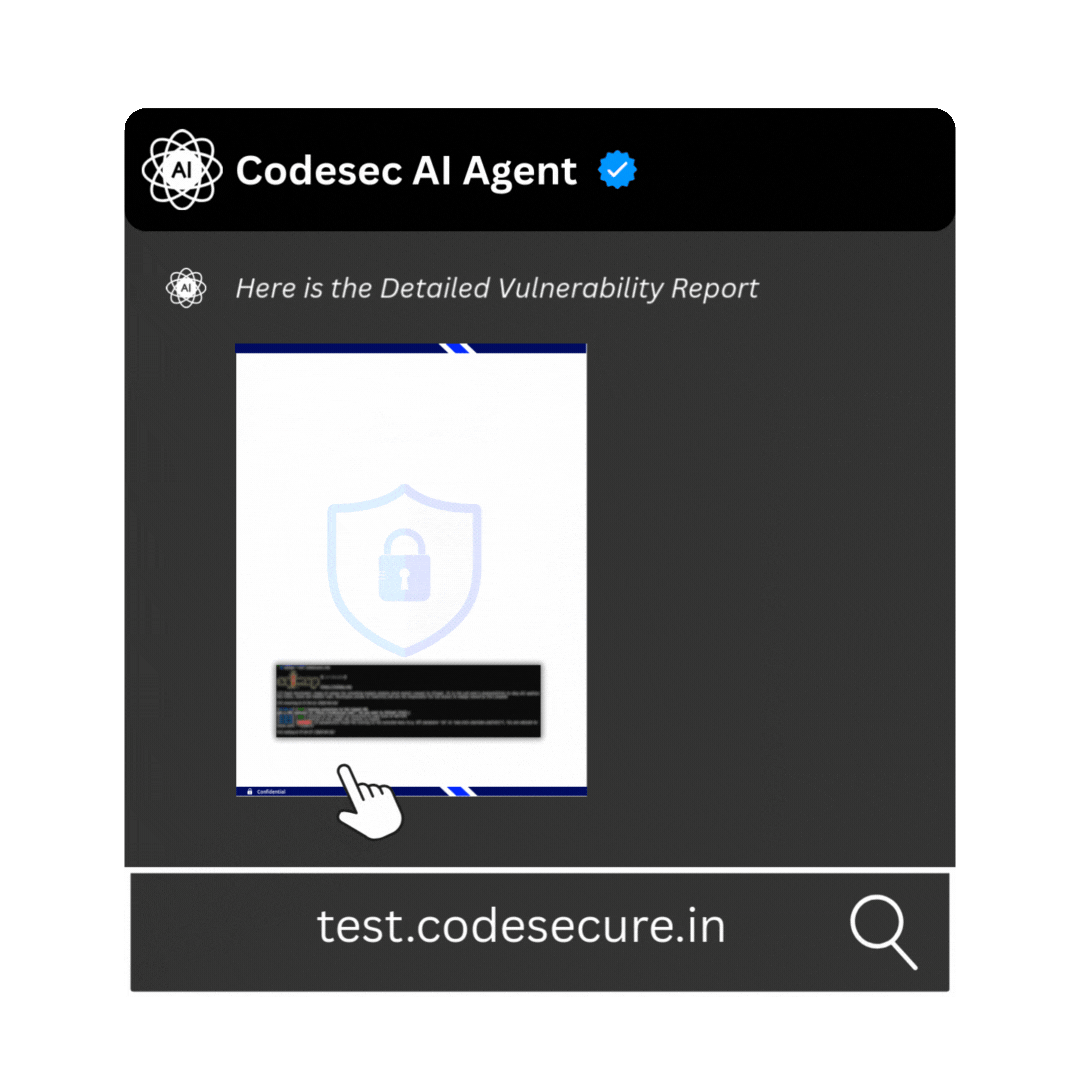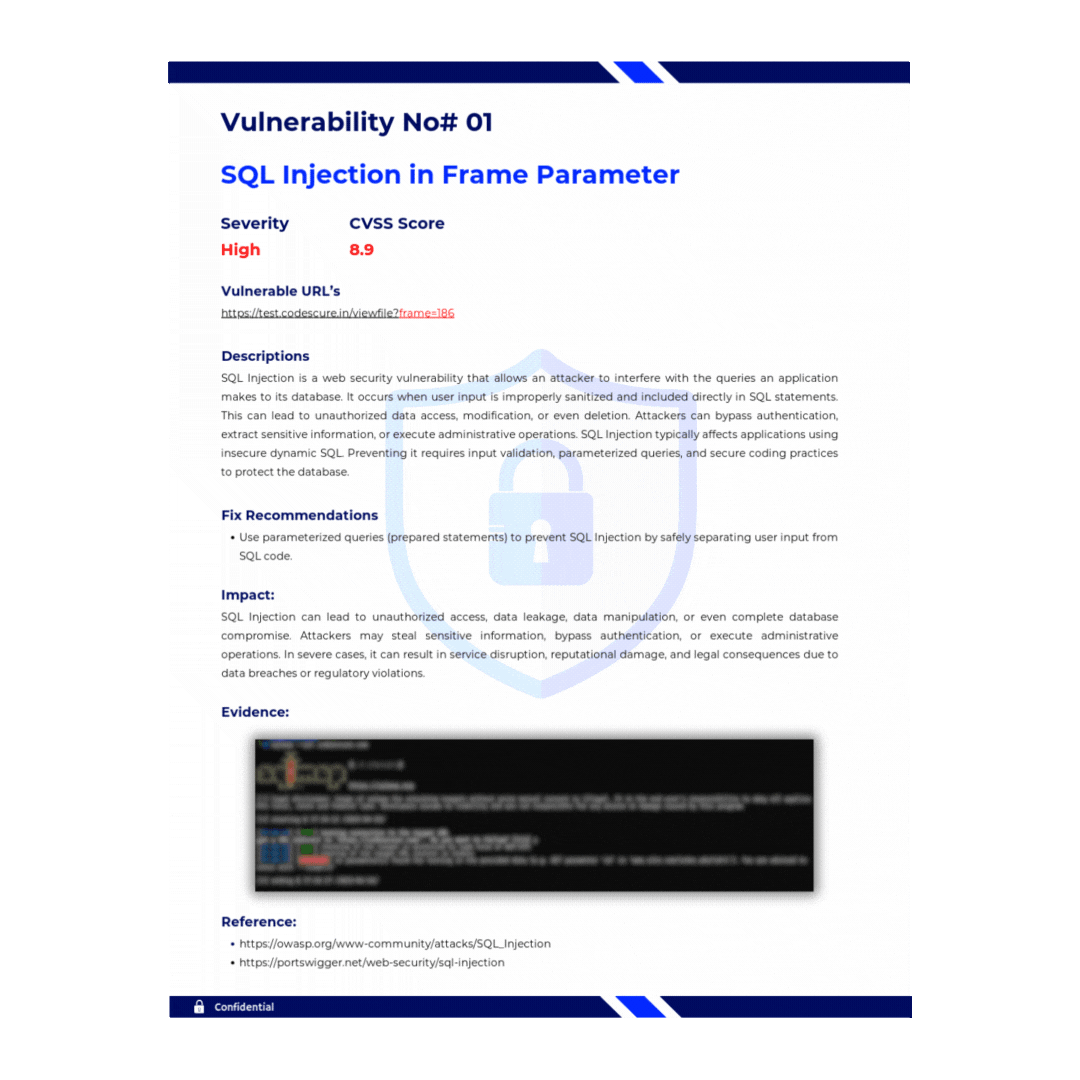
AI - Driven Vulnerability Reports
Turn Scan Data into Smart Reports — Powered by Codesec AI Agent
Say goodbye to tedious report writing — our AI crafts precise, professional, and tailored vulnerability reports in seconds, so you can focus on fixing, not formatting.